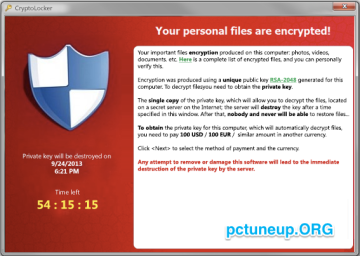
CryptoLocker is a strain of ransomware that targets
the Windows operating systems first spotted in September 2013.
When CryptoLocker infects a computer it encrypts in place files on the target computer and then displays a ransom message demanding payment within a certain amount of
time. Unlike many other strains of ransomware, CryptoLocker is well done and does exactly as it says. The files are securely encrypted and the decryption key is never on the
host machine and so can never be decrypted unless the ransom is paid. The files are reliably unencrypted upon payment and the countdown is real, payment cannot be made after it expires. There are
several different variants, each with a different ransom amount (either 100 or 300 USD) and countdown times (100 or 72 hours).
Removing the virus does not restore the encrypted files and may make it more difficult to pay the ransom. Most anti-virus software does not catch it until it is too late and the encryption is fully or partially complete. The program was initially spread though email attachments.